What is SIEM?
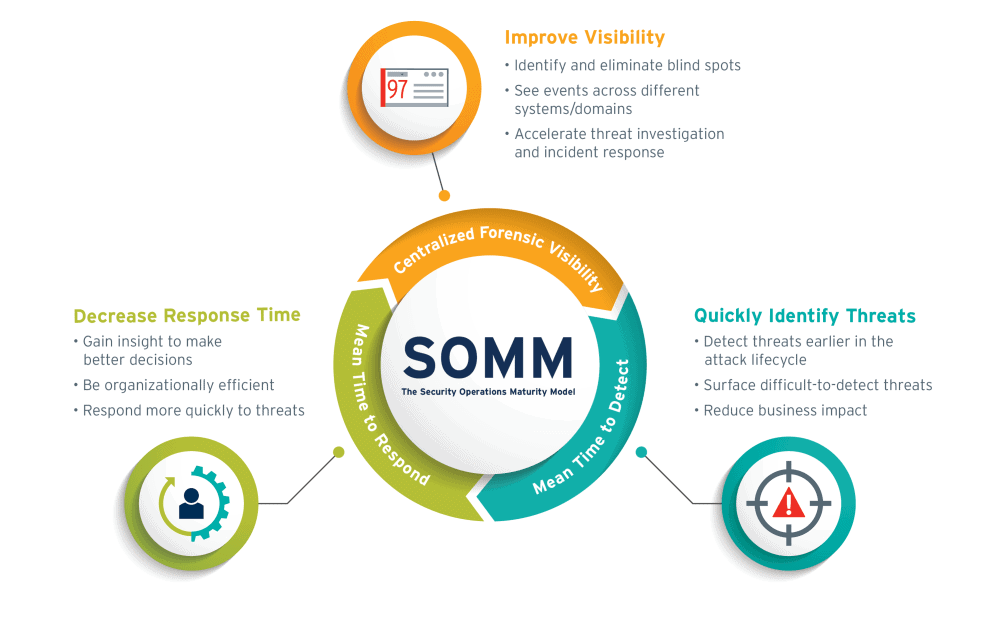
At its most fundamental level, a SIEM solution enables an organization to centrally collect data across its entire network environment to gain real-time visibility into activity that may potentially introduce risk to the organization.
Using SIEM technology to achieve visibility into network activity helps organizations address issues before they become a significant financial risk. It also helps operations better manage company assets.


 RSS Feed
RSS Feed