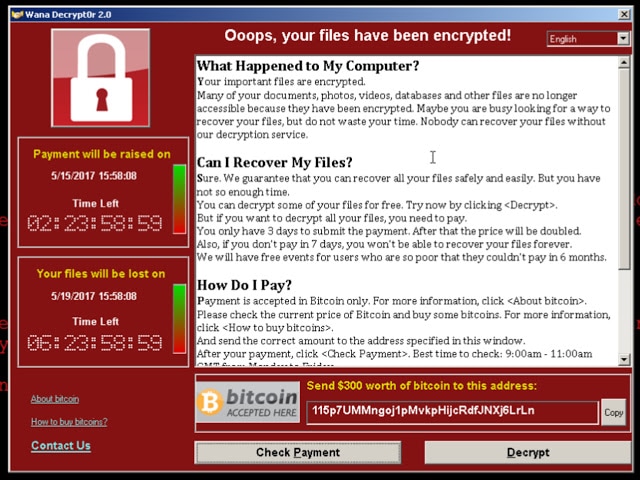
| A major ransomware attack has affected many organizations across the world reportedly including Telefonica in Spain, the National Health Service in the UK, and FedEx in the US. The malware responsible for this attack is a ransomware variant known as 'WannaCry'. The malware then has the capability to scan heavily over TCP port 445 (Server Message Block/SMB), spreading similar to a worm, compromising hosts, encrypting files stored on them then demanding a ransom payment in the form of Bitcoin. It is important to note that this is not a threat that simply scans internal ranges to identify where to spread, it is also capable of spreading based on vulnerabilities it finds in other externally facing hosts across the internet. | لقد أثر هجوم الفديه الكبير واناكراي على العديد من المنظمات في جميع أنحاء العالم بما في ذلك تلوفونيكا في إسبانيا، وخدمة الصحة الوطنية في المملكة المتحدة، و فيداكس في الولايات المتحدة. البرمجيه الخبيثة المسؤولة عن هذا الهجوم كانت هجوم الفديه البديل المعروف باسم واناكراي البرمجيه الخبيثة "واناكراي" كان لديها القدرة على مسح المنفذ تي سي بي 445 بشكل كبير وهو المسؤول عن (خادم حجب الرسائل اس ام بي). "واناكري" انتشر بشكل مماثل لطريقه انتشار الدوده وورم، انتهك اجهزه المضيفين، شفر الملفات المخزنة على هذه الاجهزه ثم طالب بدفع فدية ماليه على شكل بت كوين (العملة الرقمية التي يمكن التداول بها في المعاملات دون الحاجة إلى البنك المركزي). من المهم أن نلاحظ أن هذه البرمجيه الخبيثه ليست ببساطة تهديدا يقوم بمسح النطاقات الداخلية لتحديد المكان التي ستنتشر بها فقط، بل هو أيضا قادرة على نشر نفسه من خلال نقاط الضعف او الثغرات التي يجدها على اجهزه المضيفين التي يتمكن من الوصول اليها في النطاقات الخارجيه عبر الإنترنت |
ترجمة بالعربية لتغطية سيسكو تالوس لـ واناكراي Arabization for Cisco Talos coverage for WannaCry16/5/2017
0 Comments
Software Applications are at the core of every business. Today’s organizations deploy a myriad of web applications, ranging from external-facing corporate websites to internal-facing portals.
WhiteHat Sentinel Dynamic is a Software-as-a-Service platform that enables your business to quickly deploy a scalable web application security program. No matter how many websites or how often they are updated, Sentinel Dynamic can scale to meet any demand. Protect your network from malwareGet the market's only network-based malware defense that goes beyond point-in-time detection to protect across the entire attack continuum. Designed for our network security appliances, specifically the Next-Generation Intrusion Prevention System (NGIPS), AMP for Networks provides visibility and control to protect against highly sophisticated and targeted advanced malware.
|
AlJammaz Distribution
|




 RSS Feed
RSS Feed