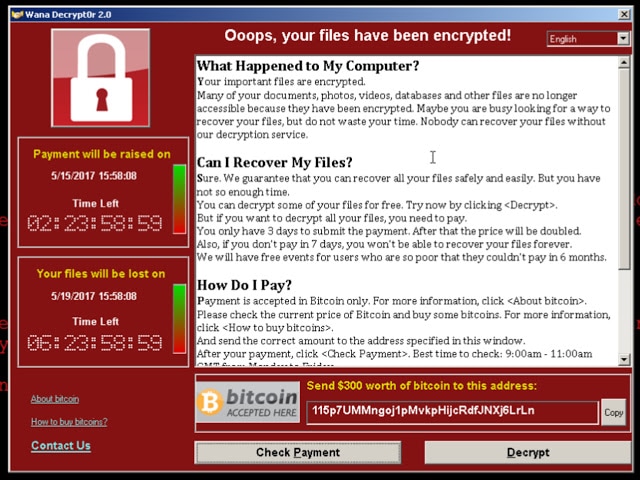
| A major ransomware attack has affected many organizations across the world reportedly including Telefonica in Spain, the National Health Service in the UK, and FedEx in the US. The malware responsible for this attack is a ransomware variant known as 'WannaCry'. The malware then has the capability to scan heavily over TCP port 445 (Server Message Block/SMB), spreading similar to a worm, compromising hosts, encrypting files stored on them then demanding a ransom payment in the form of Bitcoin. It is important to note that this is not a threat that simply scans internal ranges to identify where to spread, it is also capable of spreading based on vulnerabilities it finds in other externally facing hosts across the internet. | لقد أثر هجوم الفديه الكبير واناكراي على العديد من المنظمات في جميع أنحاء العالم بما في ذلك تلوفونيكا في إسبانيا، وخدمة الصحة الوطنية في المملكة المتحدة، و فيداكس في الولايات المتحدة. البرمجيه الخبيثة المسؤولة عن هذا الهجوم كانت هجوم الفديه البديل المعروف باسم واناكراي البرمجيه الخبيثة "واناكراي" كان لديها القدرة على مسح المنفذ تي سي بي 445 بشكل كبير وهو المسؤول عن (خادم حجب الرسائل اس ام بي). "واناكري" انتشر بشكل مماثل لطريقه انتشار الدوده وورم، انتهك اجهزه المضيفين، شفر الملفات المخزنة على هذه الاجهزه ثم طالب بدفع فدية ماليه على شكل بت كوين (العملة الرقمية التي يمكن التداول بها في المعاملات دون الحاجة إلى البنك المركزي). من المهم أن نلاحظ أن هذه البرمجيه الخبيثه ليست ببساطة تهديدا يقوم بمسح النطاقات الداخلية لتحديد المكان التي ستنتشر بها فقط، بل هو أيضا قادرة على نشر نفسه من خلال نقاط الضعف او الثغرات التي يجدها على اجهزه المضيفين التي يتمكن من الوصول اليها في النطاقات الخارجيه عبر الإنترنت |
ترجمة بالعربية لتغطية سيسكو تالوس لـ واناكراي Arabization for Cisco Talos coverage for WannaCry16/5/2017
0 Comments
The Veritas NetBackup™ 5240 Appliance is a fully integrated Enterprise backup appliance with expandable storage and intelligent end-to-end deduplication for physical, virtual and cloud environments. Only Veritas appliances deduplicate on both the client and target side.
Veritas NetBackup™ 5240 Appliance delivers greater capacity, density and performance to reduce customers’ operating and capital expenditures. As a purpose-built backup appliance (PBBA), it enables the ability to address customers’ data center challenges while simplifying data protection needs. Do More with Less, The Cisco BE6000 family provides complete collaboration capabilities and services that bring people closer together on any device, from any location, at any time. Its comprehensive, open, and interoperable architecture lets small & midsize businesses fulfill specific needs securely and efficiently with less hardware and reduced IT complexity and costs.
Cisco Business Edition 6000 (BE 6000) is designed for small to midsized companies with a work-force of up to 1000 workers. The standard features include high-quality voice and video communications, instant messaging capabilities, multi-user conferencing, and contacts at your fingertips, all incorporated into one device. Linksys Business Wireless-AC Series Delivers enterprise-grade software features for the SMBs7/3/2016 STAY CONNECTED THROUGHOUT THE OFFICEAs mobile computing and communication become standards of the modern workplace, the need for a more efficient wireless network grows by the day. Linksys offers a wide range of wireless access points for secure, high-speed wireless connectivity with advanced security and management features, so your employees can stay connected across the office. GREATER RANGE, ENHANCED MANAGEMENT FEATURES, BETTER OVERALL PRODUCTIVITY Smart devices are playing a critical role in influencing customer decisions and behaviors. While Wi-Fi devices have become an absolute requirement for customers and employees, small to midsize businesses (SMBs) are challenged to deploy
a reliable wireless network within a limited budget and little to no IT staff. Ruckus Unleashed is a controller-less wireless LAN solution that enables SMBs to deliver an optimal wireless experience at an affordable price point. Configured in 60 seconds and deployed in minutes, Ruckus Unleashed eliminates the complexity pitfall of a controller-based WLAN. With easy migration options to the Ruckus ZoneDirector, SmartZone or future Ruckus platforms, Ruckus Unleashed scales with your business. Now SMBs can deliver a Wi-Fi user experience with high RF performance and network resiliency. |
AlJammaz Distribution
|







 RSS Feed
RSS Feed